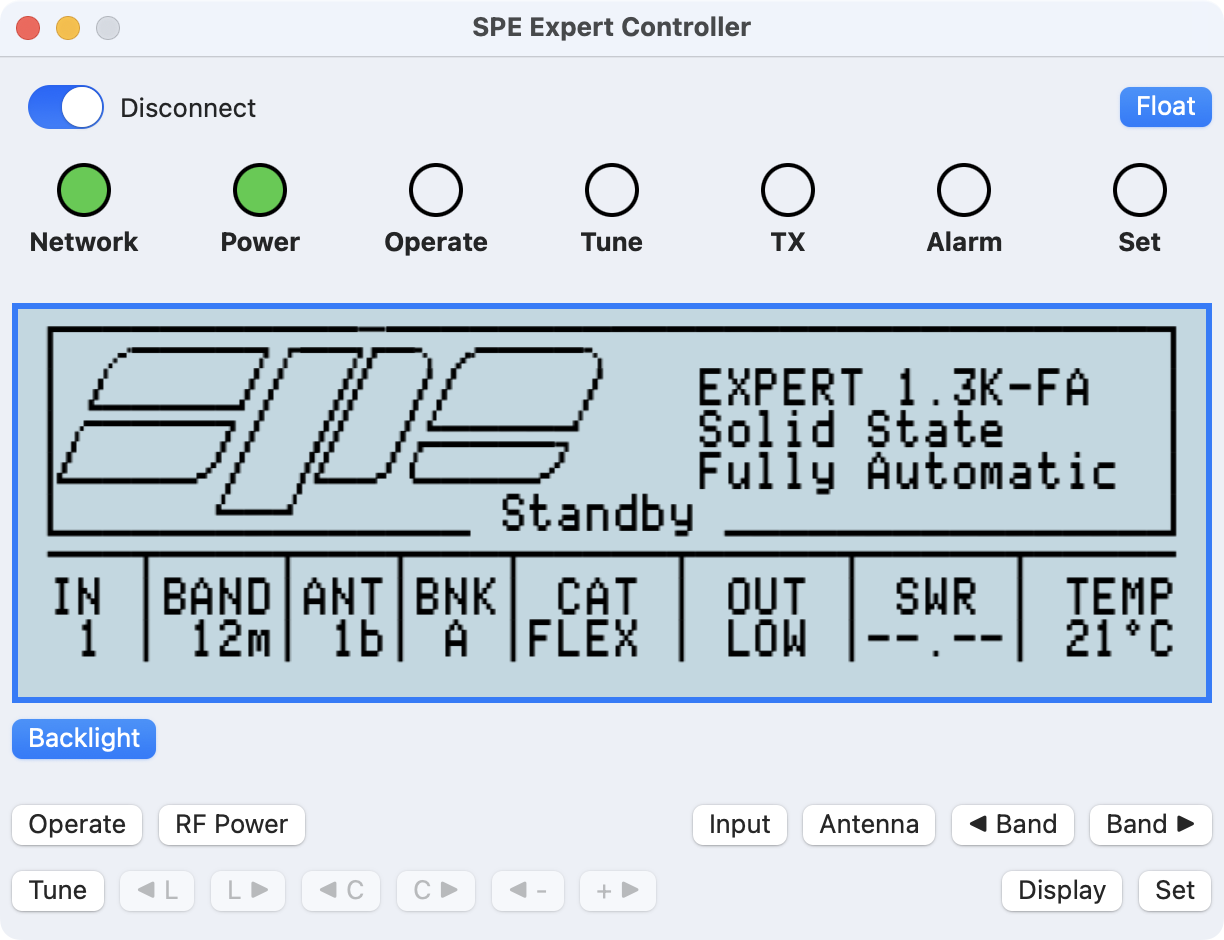
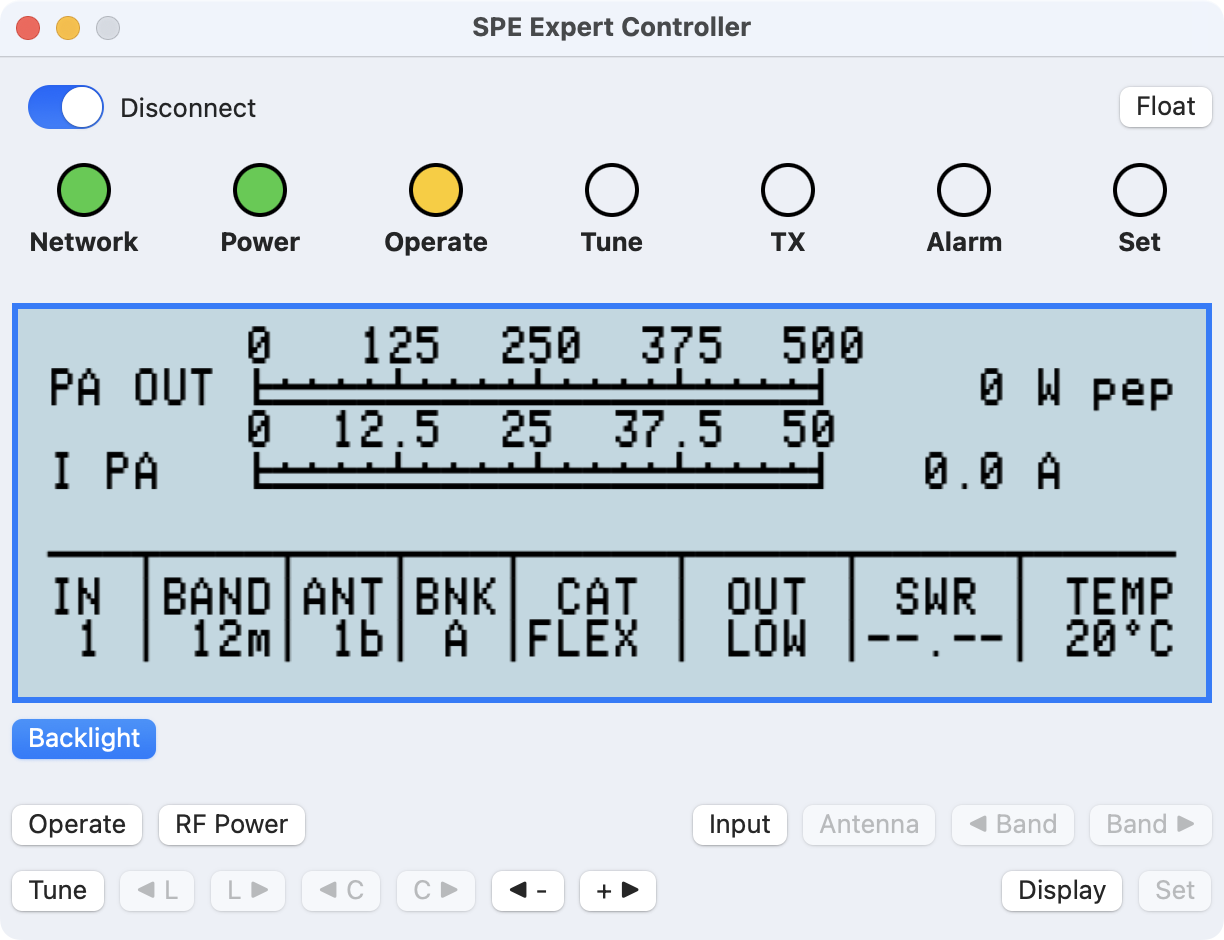
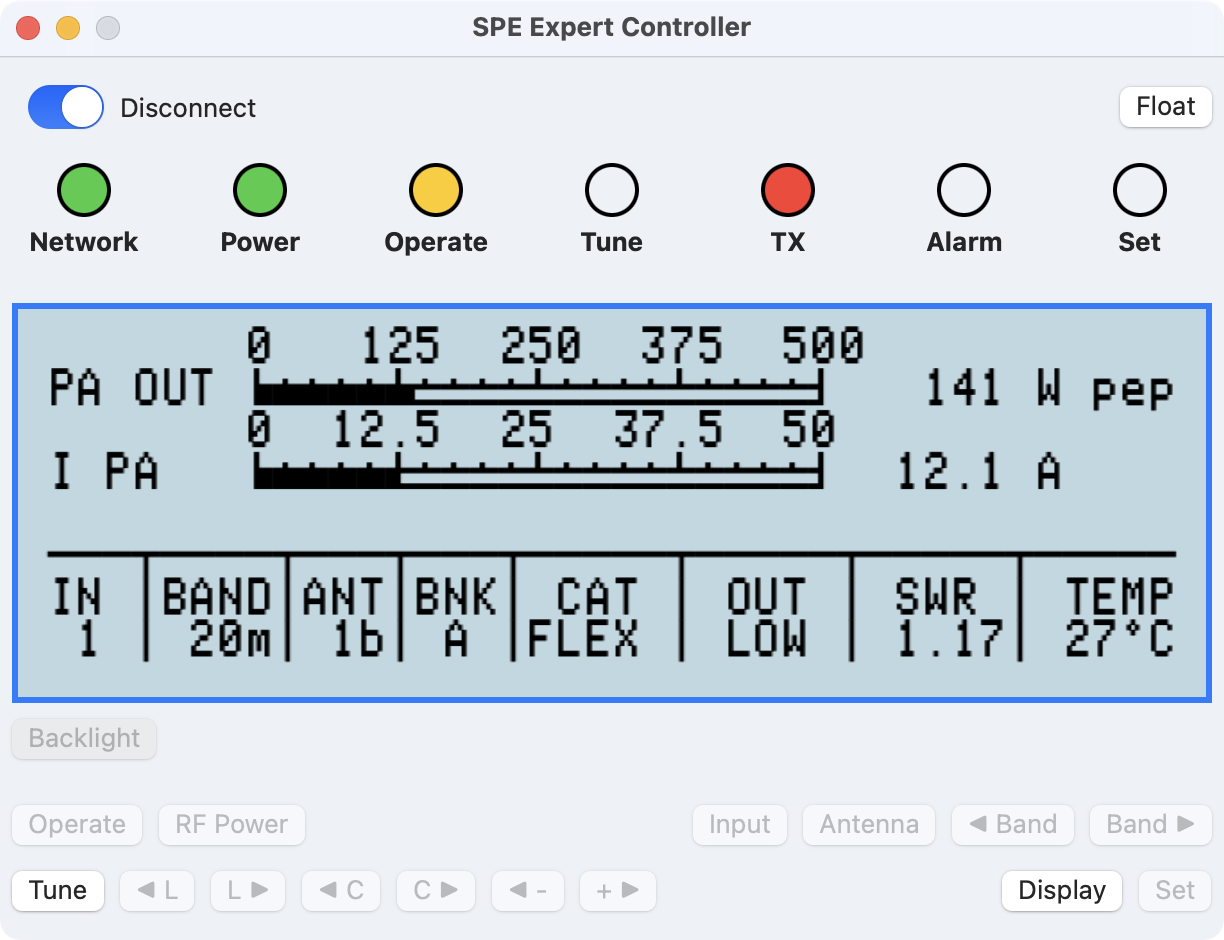
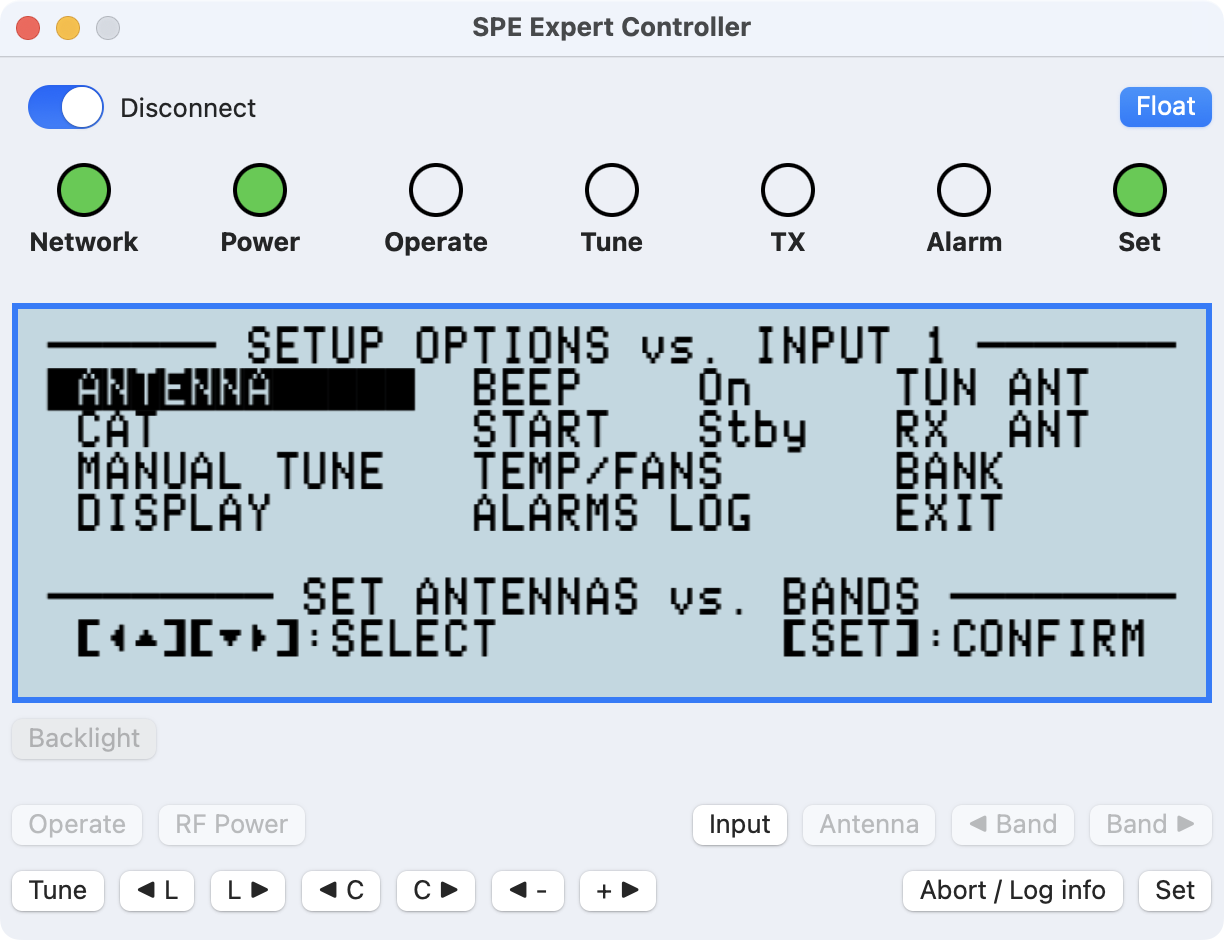
Select a button to access further information.
This page contains the following contents:
- What is a Network/Serial adapter and why might I need one?
- Adapters known to work with SPE Expert Controller
- Other adapters
- Network security.
What is a Network/Serial adapter and why might I need one?
A network / serial adapter provides a bi-directional bridge between a network technology – e.g. Internet Protocol (IP) – and a serial – e.g. RS-232 – technology. In the context of macOS and a SPE amplifier, the bridge is between TCP/IPv4 or TCP/IPv6 and the RS-232 standard.
The SPE range of amplifiers do not support a network technology, only serial so we must connect to an amplifier using either USB or RS-232.
Both USB and RS-232 require a wired connection between the computer, in our case a Mac, and the SPE amplifier. That imposes a couple of constraints. Distance, as cable length has upper limits and physical cable connectivity. i.e. there must be a cable between the Mac and SPE amplifier.
IP networks also have cable length constrains but through the use of switches, routers, media converters etc this constraint is effectively eliminated. The ubiquitous nature of Wi-Fi removes the need for physical cabling and thus enables network connectivity whilst roaming an environment.
Introducing a network/serial adapter between the Mac on which SPE Expert Controller is running and an SPE amplifier opens the door to managing the amplifier from any location where Mac and SPE amplifier are inter-connected by an IP network. That network may be global and contain wired, wireless, terrestrial and space segments.
Adding a network/serial adapter, adds threat vectors which can be exploited by mal-actors, hackers, malware etc. So, before adding a network/serial adapter between your amplifier and Mac you should consider most carefully the risks, impacts and ensure you introduce protective measures. Please read the section below entitled: Network Security.
Adapters known to work with SPE Expert Controller
The table below details the make and model of adapter known to work with SPE Expert Controller.
Please let me know if you have tried a different adapter and found it to work or not work with SPE Expert controller.
| MAke | Model | Date tested | Comments | Suppliers |
|---|---|---|---|---|
| Waveshare | RS232/485/422 To RJ45 Ethernet Module, TCP/IP To Serial, with POE Function | March 2025 | Serial cable wiring | Amazon |
Other adapters
The table below details the make and model of other adapter thought to work but which have not been tested with SPE Expert Controller.
| Make | Model | Comments | Suppliers |
|---|---|---|---|
| Moxa | NPort 5110A | NPort 5100 series also | Amazon |
| Waveshare | Industrial serial server. RS232 to RJ45 Ethernet, TCP/IP to serial, rail-mount support, with POE function(optional) | Amazon | |
| Waveshare | RS232 RS485 to RJ45 Ethernet Serial Server, RS232 And RS485 Dual Channels Independent Operation, Dual Ethernet Ports | Amazon | |
| PUSR | USR-TCP232-302 | Amazon | |
| PUSR | USR-TCP232-306 | Amazon |
Network security
Using an adapter adds attack vectors to your network and thus everything to which that network is connected. A compromised adapter may not only malfunction but it may be used as a pivot to attack other network connected, even serially attached, devices.
Many adapters originate from China/Taiwan and there is little/no information about how security was considered in their software, the manufacturers quality assurance procedures, the vulnerabilities they may contain or procedures for the update/patching of identified defects and vulnerabilities during their lifetime.
The web-based administration interface of the tested Waveshare adapter was accessible using the unencrypted HTTP protocol only and it had no password set by default. Today, a strong password should be set by default although, in this case as it uses HTTP rather than the encryption supporting HTTPS, a password is of much less value. Alone these highlight the level of consideration given to network security in its design. Although that is only one adapter, it’s probable that many other adapters have given scant consideration to security in their design and thus contain opportunities for exploitation by mal-actors.
Using an adapter should be considered a threat to network security and considerable thought should given to their use, software update and deployment. This should include: Never exposing their network interface directly to the Internet, placing them on a segregated network and applying strict firewall rules regarding the types of traffic they can send/receive and with what devices, including those on the Internet. If an adapter is to be reachable from the Internet its interface and traffic must be protected using solutions such as an encrypted virtual network or an overlay network.
It’s very important to apply protective measures when deploying such security weak devices to a network. This is especially important if they have any sort of Internet access or access to networks were similar low-trust devices, such as IoT devices, are connected.